Other Posts In This Series
The Best Defense is a Good Offense?
Org admins are commonly tasked with managing hundreds, even thousands of users. They control and meter access to powerful functionality and valuable data using dozens, even hundreds, of permission sets and profiles. When something goes wrong because of this allowance, whether accidental or on purpose, serious damage can result.
Gandhi once said:
Nobody can hurt me without my permission.
At the end of the day, users do what they have been permitted to do. The responsibility falls on the admin’s shoulders to avert disaster. Stakes are high! While Salesforce has made efforts to mitigate these challenges, results have been mixed.
Tython Permissions Assistant aims to equip admins with comprehensive means to manage user access. “Good defense” is seizing the initiative and heading off unwarranted access. This post takes a detailed look at Permission Search, a tool to gain initiative by quickly identifying HOW and TO WHOM specific permissions have been granted.
Establish Search Parameters
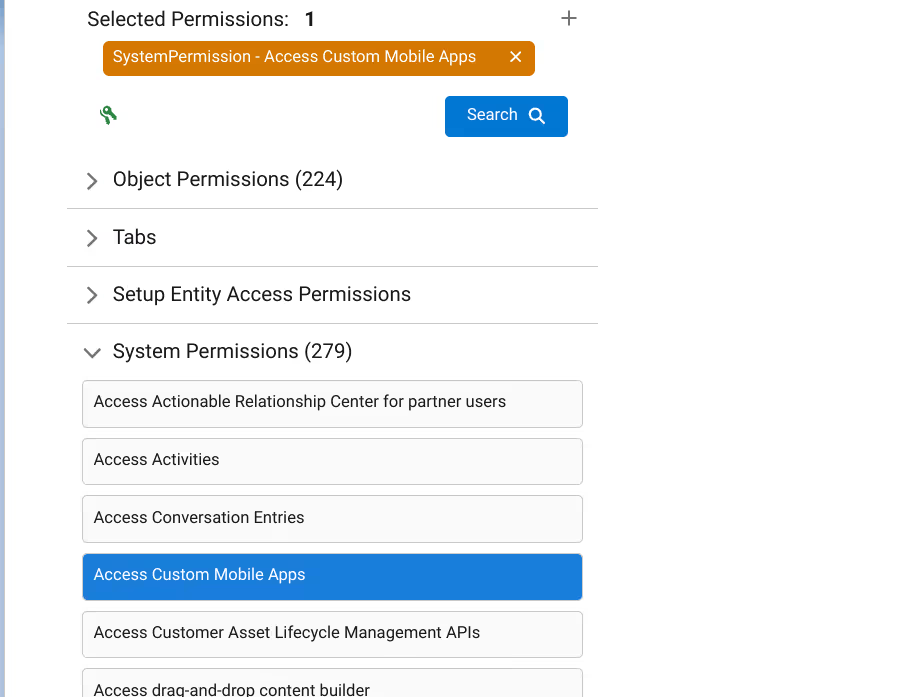
Permission Search reveals what permission sets and profiles grant access to a target you specify. Step one is to select the potentially perilous permission. Selection is as easy as a few clicks or keystrokes.
When the page loads you are greeted with a permission tree. Within this tree are all* of the items that can be made accessible via permission sets and profiles, organized by category. Simply drill into the category of permission you want to target. Even fine-grained targets, such as “Read” or “Edit” access on a particular custom field on a particular object, can be searched.
Once pinpointed, a quick click trains our sights on the quarry!
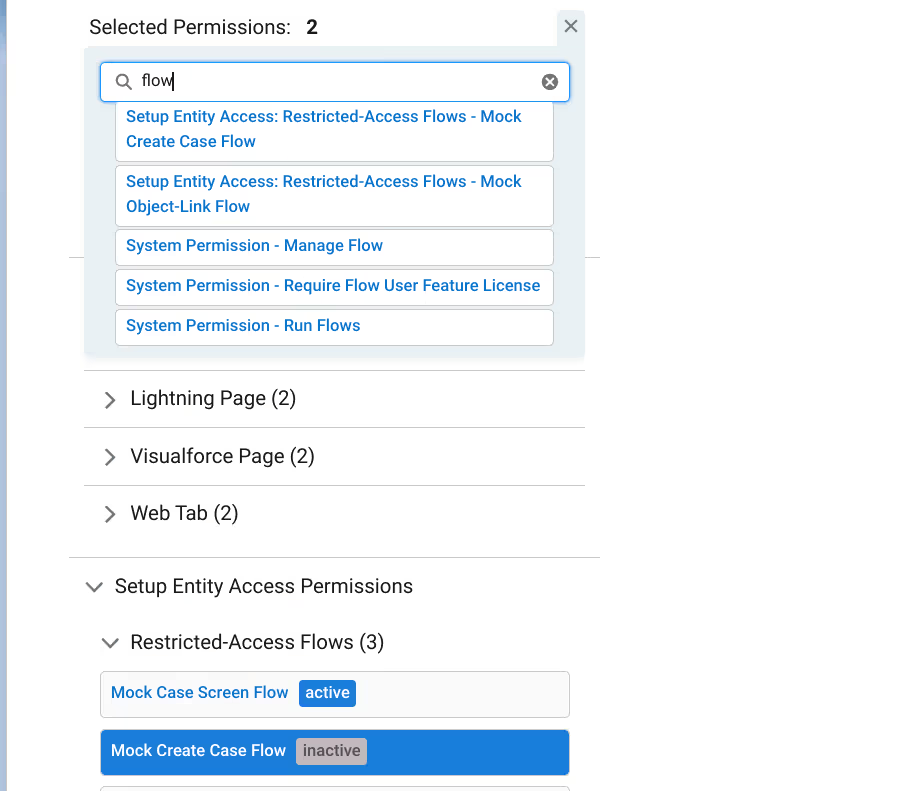
Selection can also be done by utilizing the integrated finder. Type in the target and select from the resulting list. Notice you can select multiple targets.
Before we kick off the search, there is one important option to consider.
If selecting multiple targets, “exact matches only” can be specified. This option controls whether or not resulting permission sets and profiles have to contain all of the selected permissions (“exact matches” checked) or just one (“exact matches” unchecked, the default).
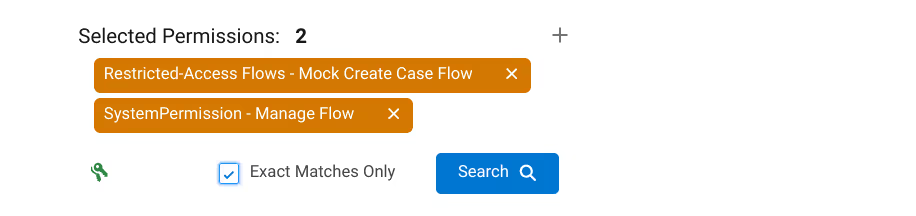
With that, the hunt is on!
Scrutinize the Round Up
Results have loaded and, like a police lineup, we have rounded up the suspects. Now we can determine without doubt where access is being granted.
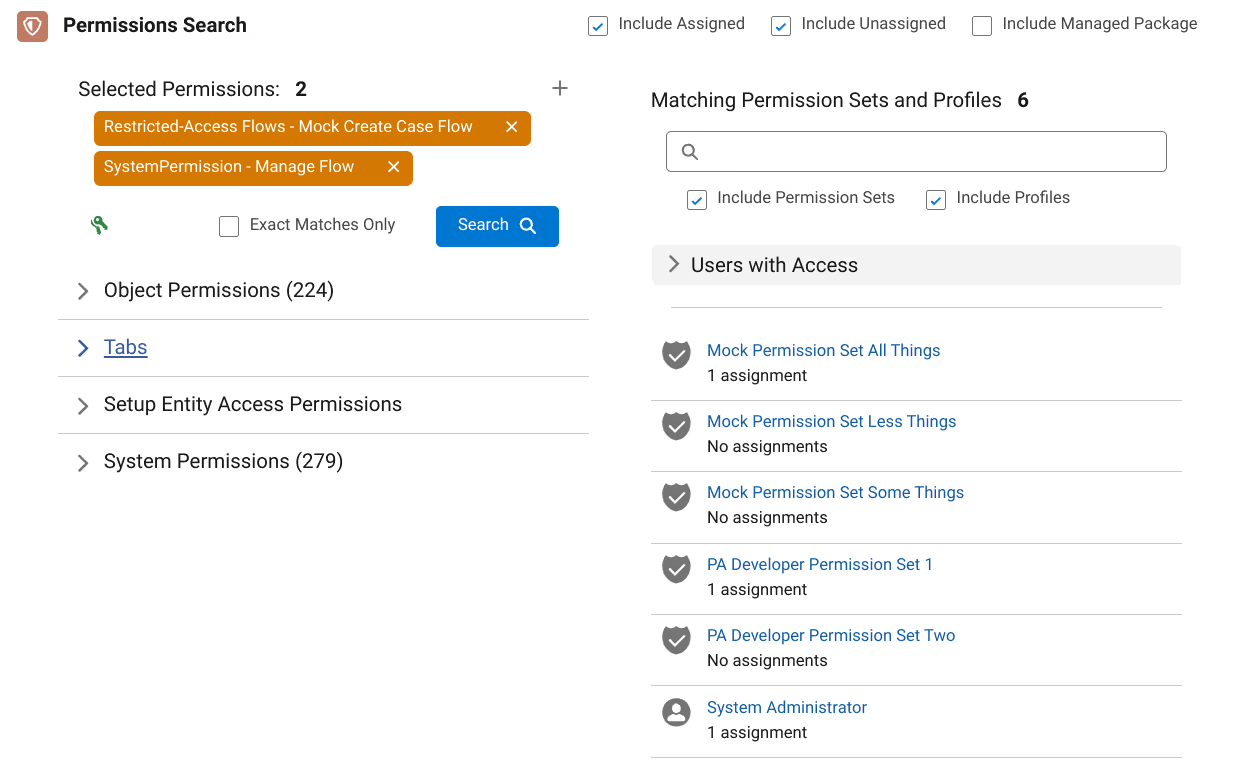
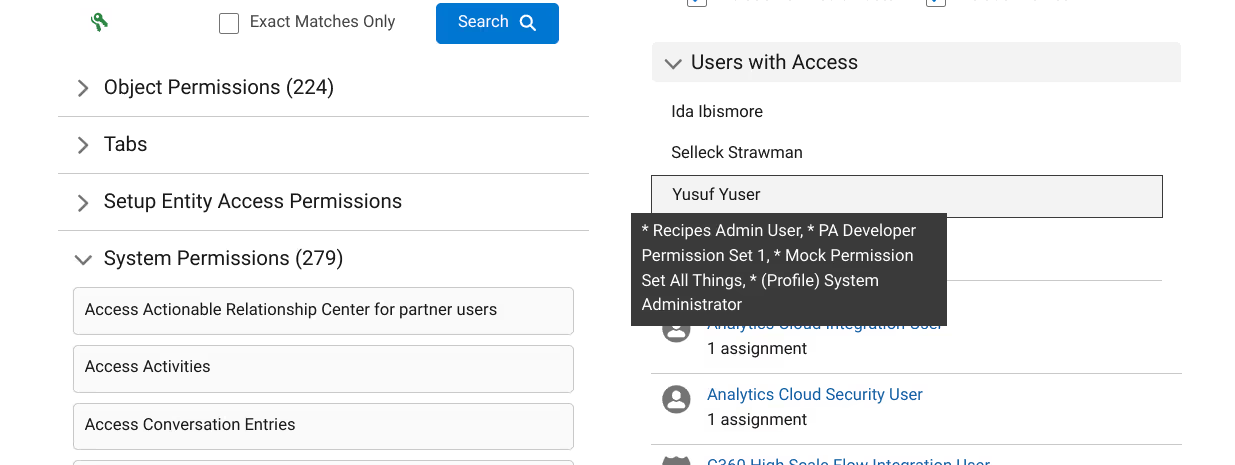
The list of permission sets and profiles contain the permission(s) we are pursuing. Clicking on these results opens up a window to further dissect the permission set or profile in detail.

If there are active user assignments, a section with a filtered list of users can be reviewed. These are the users who have been granted access to the permissions we are targeting. Click on a user in the list to view which permission sets and profiles from the search results have been assigned to them.
(Super)Power of Prevention
Some version of Peter Parker once uttered:
When you can do the things that I can, but you don’t, and then the bad things happen? They happen because of you.
The power of prevention is ultimately in the hands of admins. Tython Permission Search supercharges insight into both How a permission is enabled as well as Who holds those privileges. From here, the empowered admin can reach into their playbook and decide What actions to take.
Perhaps remove some permissions from a certain profile? Revoke a particularly precarious assignment from certain users? Clone and modify a mostly on-point permission set? Maybe even combine these results with other Permissions Assistant tools like deep User Analysis and Permission Set Similarity Analysis to do some “spring cleaning”?
Got other use cases for Permission Search? The team at Tython is always open to feedback! Interested in other tools to help deploy your offense? Reach out to request access to the Permissions Assistant beta!
* OK, almost everything. Service Providers and External Credentials are on the Todo list.
Protect Your Org.
Secure Your Data.
Salesforce security is a shared responsibility. Don't try to solve it alone.
Salesforce Updates and Guidance
Explore expert strategies and practical advice on Salesforce security and permissions





